The Federal Bureau of Investigation is offering a $10m USD reward for the capture of a Russian computer hacker responsible for launching a string of damaging cyber attacks in the U.S. and Ukraine.
The FBI have placed Amin Timovich Stigal on the Bureau’s most wanted list after allegedly conducting a series of highly damaging cyber attacks on the Ukrainian government just prior to the launch of the Russian invasion in February 2022.

The Bureau’s website is currently carrying a picture of Stigal stating that he is wanted for “conspiracy to commit computer intrusion and damage.”
FBI investigators believe the 22-year-old has been collaborating with Russia’s Main Intelligence Directorate (GRU) in targeting Ukrainian government networks, including those of the Ministries of Foreign Affairs, Education and Energy.
U.S. government computers, including sites maintained by a Maryland agency, were also targeted, and a cyber attack was carried out on the transport infrastructure of what is described as an unnamed Central European ally.
According to the FBI, Stigal allegedly created accounts on computer systems belonging to a U.S.-based messaging and communications company which he then used to carry out the attacks. The accounts were then used to scan numerous public websites of the Ukraine government to identify vulnerabilities for attack.
The attacks used malware, a malicious software designed to cause disruption to a device, referred to as “WhisperGate”.
WhisperGate included a fake ransomware message that tricked people into paying to “unlock” their files, but instead it actually deleted everything. Data was destroyed and could not be recovered, even if the ransom of $10,000 was paid.
Linda Zecher, the CEO of the Cyber Security company IronNet, told National Security News: “This is a classic and highly effective form of a cyber attack from a hostile state – in this case Russia, which is effectively sub-contracting out cyber warfare. WhisperGate is a very damaging type of malware and every government organisation and corporation should be aware of the risk.
“IronNet believes that collective defense is the best way to prevent these attacks from damaging networks. Cyber attacks are only going to get more sophisticated and damaging which is why a robust defence network is vital.”
According to the court records, Stigal and his conspirators in the GRU stole and leaked data belonging to thousands of Ukrainian citizens, which included criminal and medical records. This was described as an attempt to spread fear about the security of government systems and Ukrainian’s personal information before Russia’s invasion.
Websites were also defaced with the following message: “Ukrainian! All the information about you has become public, be afraid and expect the worst. This is for your past, present and future.”
An arrest warrant was issued in Maryland on June 25, 2024, charging Stigal with conspiracy to commit computer intrusion and damage.
Merrick B. Garland, Attorney General, said in a statement: “The defendant conspired with Russian military intelligence on the eve of Russia’s unjust and unprovoked invasion of Ukraine to launch cyberattacks targeting the Ukrainian government and later targeting its allies, including the United States.”
Stigal was born in Grozny, Chechnya on 1 October 2002. His social media, dominated by cat profile pictures, offers little insight into the man behind the keyboard of the alleged cyber attacks.
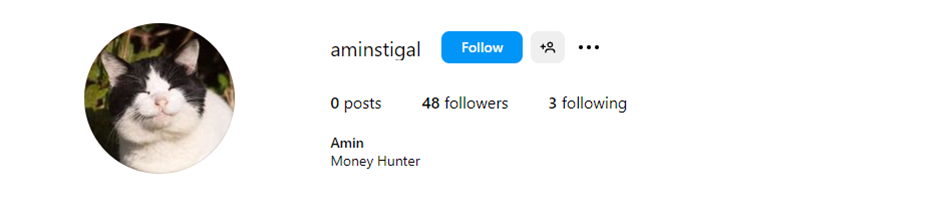
National Security News (NSN) identified an Instagram account linked to Stigal, with a biography that reads “Money Hunter”.
A Pinterest account offered another name, “Gadkiy Chechen” which translates to Nasty Chechen.
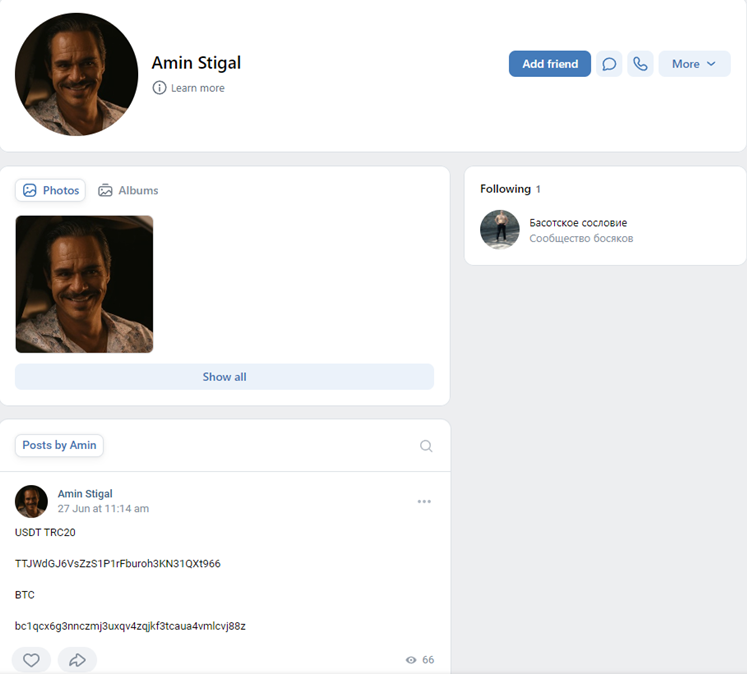
NSN also found a recent profile on VK, a Russian social media platform, with the username “fearoftheemperor.” The profile itself offered little information, but it included a post from June 27th – just two days after Stigal’s arrest warrant was issued. The post listed two cryptocurrency addresses, currently empty of funds.
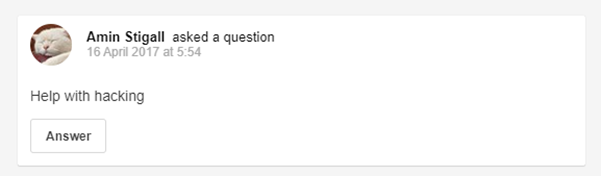
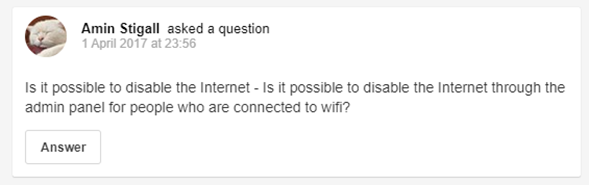
Another social media profile was found to be last active on the same date as the VK account. Historic posts from this account in 2017 refer to hacking and asking questions on how to disable someone’s internet.
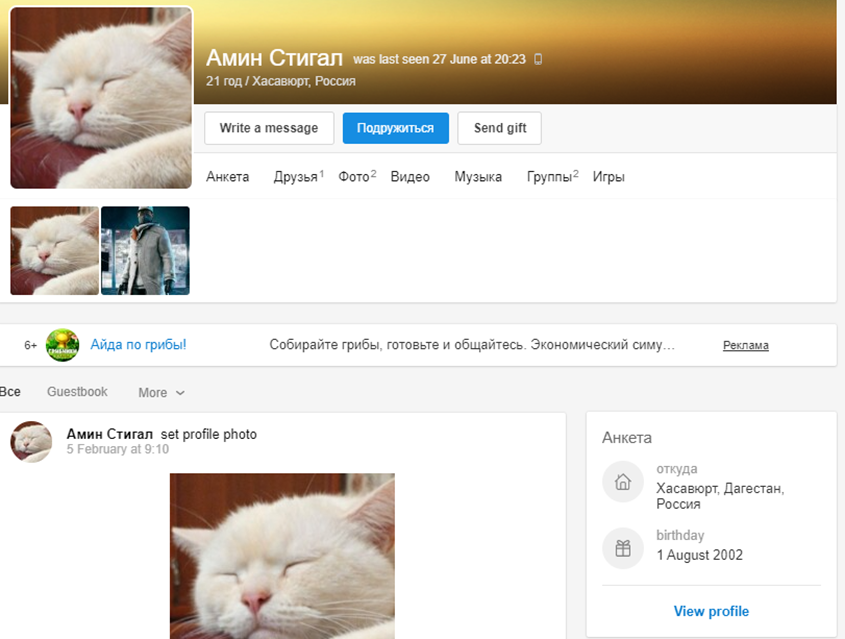
NSN also identified an older VK profile, possibly belonging to Stigal due to a matching fabricated birthdate with FBI records. The profile, however, offered little beyond a connection to a secondary school in Khasavyurt, Dagestan, an area to which Stigal has connections, according to the FBI.
Reports indicate Stigal’s father, Tim Vakhaevich Stigal, is also wanted in the U.S. in connection to separate cyber crime activity.
In January 2024, Tim Stigall was accused of hacking into computers to steal debit and credit card and personal data associated with cardholders. He is alleged to have targeted companies based in Pennsylvania, California and Virginia.
The U.S. Department of Justice said: “[Tim] Stigal additionally transmitted a threat to impair the confidentiality of stolen personal data belonging to customers of the corporate victim if a ransom was not paid to Stigal.”
Unlike his son, Tim Stigal does not hide his online presence, NSN identified accounts on various platforms, and a website, where Tim posts about Forex trading and cryptocurrency. He has also written book on trading and Islam, and ancient mythology.

























































































































































































































































































