
Traditional background checks for employees are not good enough anymore as sophisticated state actors use stolen identities and artificial intelligence to get around security checks. Even a cyber security training firm discovered their new software engineer was actually a North Korean hacker. The hacker was exposed after he attempted to load information-stealing malware onto company systems.
Alberto Casares, the chief technology officer at the cyber security company Constella Intelligence, told National Security News that this threat is not new and “underscores the sophistication and persistence of state-backed actors.”
He explained: “The evolving landscape of cyber threats, including the recent case, underscores the limitations of traditional background checks and ID validation processes.
“These conventional methods are increasingly inadequate in detecting sophisticated attempts by threat actors to infiltrate organisations.
“As cybercriminals leverage AI to create more convincing fake identities and deception tactics, it’s clear that more advanced detection methods are needed.”
According to Casares, it is crucial to “integrate systems that can validate whether an identity has been previously compromised,” and assess risk based on provided personal information.
Casares explains that Constella employs this method and offers it to other companies for integration into hiring, onboarding, or registration processes. He said this is effective because “an individual’s digital footprint is difficult to alter, providing a reliable indicator of potential risk.”
Casares added that these state actors “have the resources and time to execute complex and covert operations, using realistic personas to infiltrate organisations. This represents a shift from traditional cyberattacks to more nuanced tactics.”
A security firm infiltrated
Stu Sjouwerman, the CEO and president of KnowBe4, the targeted company, said: “We posted the job, received resumes, conducted interviews, performed background checks, verified references, and hired the person. We sent them their Mac workstation, and the moment it was received, it immediately started to load malware.”
The hacker is believed to be part of what is known as a “laptop farm” – a large-scale operation where North Korean hackers use stolen identities and remote access to infiltrate US companies.
The way the scam work, Sjouwerman explained, is the fake worker gets their workstation sent to an address linked to the “IT mule laptop farm”. They then use a VPN to mask their true location, which is in North Korea or China, and they work late to make it look like they are working U.S. hours.

“The scam is that they are actually doing the work, getting paid well, and give a large amount to North Korea to fund their illegal programs,” said Sjouwerman.
KnowBe4’s security operations centre began to ask questions after noticing the suspicious activity on the new hire’s device.
The hacker said “he was following steps on his router guide to troubleshoot a speed issue,” however, after further probing, he became unresponsive and the company blocked his device.
According to Casares, red flags should be raised if a new hire engages in “unusual or unauthorised network activity,” particularly outside of their job scope or regular working hours. This, he said, “could indicate reconnaissance or data exfiltration attempts.”
Explaining why the attacker tried to launch malicious software on the company laptop, Sjouwerman said: “We can only guess, but the malware was an infostealer targeting data stored on web browsers, and perhaps he was hoping to extract information left on the computer before it was commissioned to him.”
The firm said that they successfully stopped the attack before any data loss and came public with the incident because “If it can happen to us, it can happen to almost anyone.”
Stolen identity used
The new hire at KnowBe4 was a real person who stole the identify of a U.S. national to pass the background checks, also using AI to alter a stock image submitted with the application.
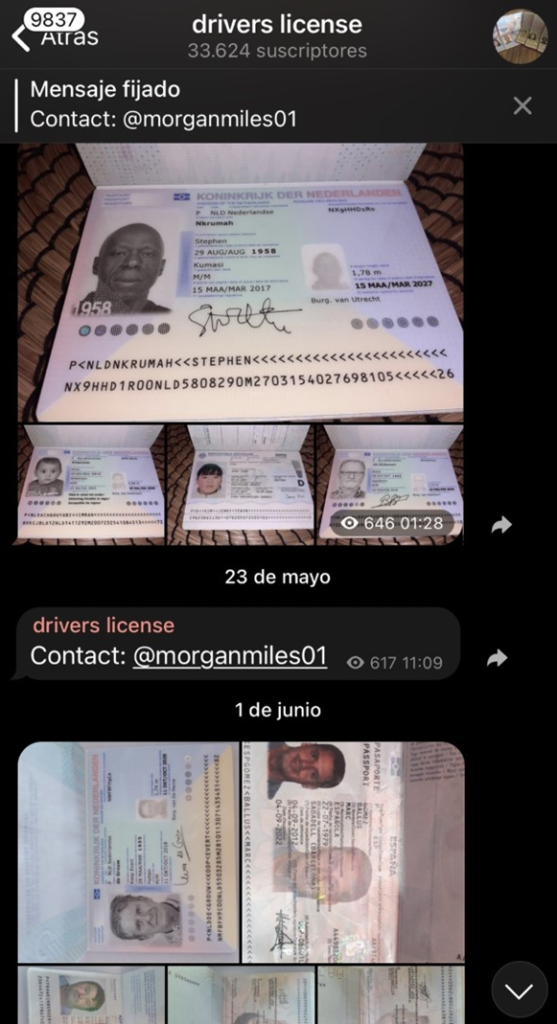
Casares told NSN: “There are underground places from Telegram to forums where you find this type of information for sale.”
“You can find people selling their online profiles, which others use to create fake identities for background checks,” added Casares.
KnowBe4 shared their investigation with Mandiant, Google’s cybersecurity subsidiary, and the FBI who have been warning of “laptop farms” since 2022.
In May 2024, prosecutors in the U.S. accused Christina Chapman and three North Korean national of setting up a laptop farm on behalf of North Korean workers. They allegedly stole the identifies of over 60 American citizens to aid foreign IT workers find remote jobs in the U.S. across 300 companies.
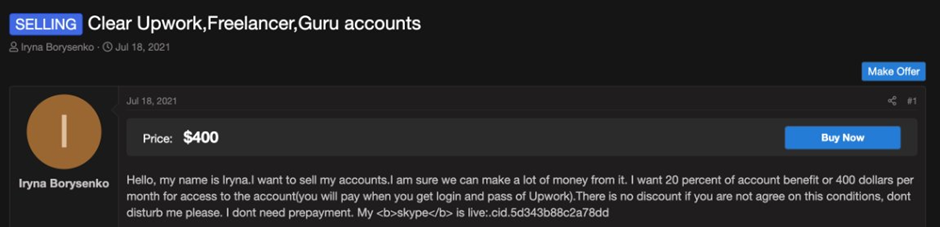
In a separate U.S. complaint, Oleksandr Didenko, a Ukrainian national, was also accused of operating a laptop farm which hosted around 79 computers in California, Tennessee and Virginia. Didenko allegedly created numerous fake accounts on U.S. IT job platforms and then sold these accounts to overseas workers, some in North Korean, to be used to apply for remote jobs.

































































































































































































































































































