China is recruiting talented citizens through local “hacking competitions” and weaponising their talents to attack Western governments, according to a report by ETH Zurich University’s Centre for Security Studies. The revelation, coupled with recent admissions by Dutch officials about the wide scope of Chinese hacking efforts, has amplified fears about China’s growing “hack-for-hire” programme.

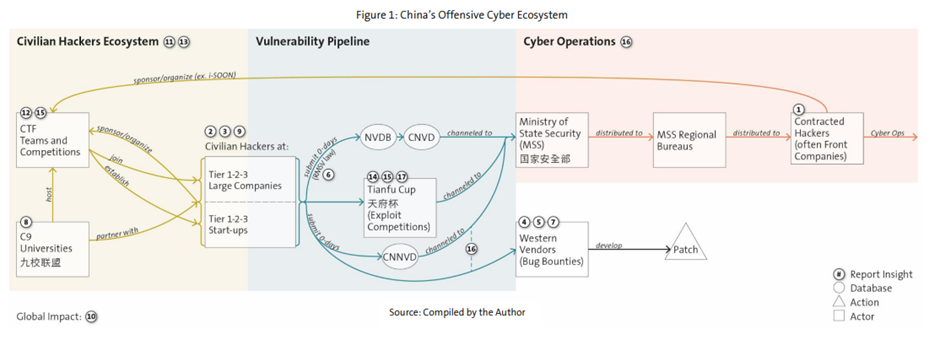
The report titled “From Vegas to Chengdu”, uncovers a two part hacker system:
- Competition Stars – The elite teams and researchers who dominate prestigious competitions with their expertise in finding system weaknesses (vulnerabilities). They often target software used by Western governments and companies, including Apple, Android, and Microsoft.
- Government-Contracted Hackers – Operating under the radar, these private contracted hackers do not compete publicly. Instead, they focus on exploiting weaknesses uncovered by the “stars” to conduct cyber espionage and steal intellectual property. The competition hackers also start businesses that develop security tools, which can then be used by the contracted hackers to complete their mission faster.
Eugenio Benincasa, report author and senior researcher, documents how Chinese security researchers began dominating international hacking competitions after 2014. At the Pwn2Own competition, Chinese teams’ winnings increased from 13% in 2014 to 79% by 2017.
Realising the strategic value, the Chinese government then banned researchers from international competitions and created domestic events. In 2018, the Tianfu Cup was founded by Chinese technology giants including Alibaba, Tencent, and Baidu.
In 2021, a new cybersecurity law was introduced, requiring Chinese citizens who discover a vulnerability to disclose it to official agencies, which are linked to the Ministry of State Security, within 2 days. This system allows the state to benefit from civilian hackers’ research without their direct involvement.
The report evidences this by describing instances where system vulnerabilities discovered at hacking competitions were identified in later cyber-attacks. For example, a vulnerability identified in Apple iOS during one of the events was used in Chinese cyber espionage campaigns against the Uyghurs, the Chinese Muslim minority in the Xinjiang region.

A data leak discussed in the report gives insight into the “hack-for-hire” system. It was revealed that Chinese security contractor i-SOON had been contracted by the government to carry out espionage operations on its behalf which spanned a period of eight years targeting 20 foreign governments.
Additionally, these same companies, such Topsec and i-SOON, are sponsors of the hacking competitions.
The report concludes that China’s cyber network, which integrates hacking contests, universities, private contractors, and intelligence agencies, is a well-orchestrated system designed to capture and use talent for state purposes.
Benincasa wrote: “The Chinese government has created an elaborate multifaceted “hack-for-hire” ecosystem that is unlike anything we have ever seen before.”
Recent international reports have also uncovered Chinese-linked hacking campaigns targeting Western governments, defence companies, and international organisations. Dutch intelligence and security authorities recently disclosed a large-scale Chinese hacking campaign, which has infiltrated thousands of computer systems worldwide. Hackers exploited a software flaw to gain access to at least 20,000 devices and may still be lurking in many systems.
Australian officials are especially worried. James Paterson, Shadow Minister for Home Affairs and Cyber Security, said Chinese cyberattacks and interference in Australian institutions have “never been more prolific.” Paterson pointed to a specific hacking group, Volt Typhoon, which has been targeting critical infrastructure like power, water, and transportation networks, as he raised concerns about potential sabotage in the future.
Linda Zecher, the CEO of the US-based cyber security company IronNet, said that collective defence against hackers was the best form of defence.
She told NSN: “This report demonstrates why governments and corporations need to ensure that their cyber security systems are up to date and can withstand the most sophisticated hacks. Hackers will adapt and evolve to break into even the most secure systems and that is why IronNet’s collective defence system offers the best protection against hostile state and non-state actors.”
The Chinese Embassy has been approached for comment.

































































































































































































































































































