
A $10 million reward is being offered for information leading to the capture of a team of Iranian hackers targeting critical infrastructure within the U.S., National Security News has learned. The move comes as the U.S. government intensifies its efforts to combat cyber threats posed by foreign adversaries.
The announcement by the State Department Rewards for Justice program, which offers rewards for information leading to the arrest of terrorists, names six Iranian security officials linked to the Islamic Revolutionary Guard Corps (IRGC).
The IRGC is a branch of the Iran’s military force which has been responsible for malicious cyber activity against the U.S. and other countries.
The hackers are accused of orchestrating cyber attacks against water, energy, and manufacturing facilities.
It is alleged that the cyber criminals hacked into programmable logic controllers (PLCs), a type of industrial computer system used to control machines, leaving devices inoperable and displaying anti-Israel messages.
The U.S. Department of State named the key players of the cyber attacks as Hamid Homayunfal, Hamid Reza Lashgarian, Mahdi Lashgarian, Milad Mansuri, Mohammad Bagher Shirinkar and Reza Mohammad Amin Saberian.

Hamid Reza Lashgarian is the head of the IRGC’s Cyber-Electronic Command (IRGC-CEC), also known as the IRGC Electronic Warfare and Cyber Defence Organisation.
The named individuals belong to a hacking group known as Cyber Av3ngers, which has been identified as a key player in the cyber attacks against PLCs made by Israel-based company called Unitronics.
Water and wastewater treatment facilities rely on PLCs to automate critical functions such as pumping, chemical dosing, data collection, and alarm systems. The systems can also be found in energy, food and beverage, manufacturing, and healthcare.
Due to their remote operation, PLCs are often internet-connected, making them targets for cyberattacks.
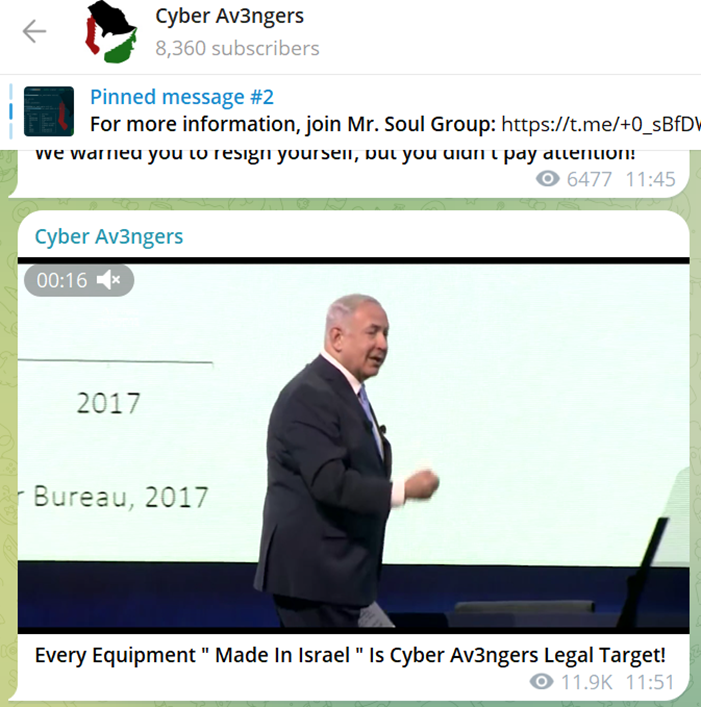
According to Dragos, an industrial cyber security company, Cyber Av3ngers were first observed in early September 2023.
In November 2023, videos on Cyber Av3ngers social media channels stated: “Every Equipment “Made In Israel” Is Cyber Av3ngers Legal Target!”
This followed a claimed cyber attack on ten Israeli water treatment systems the previous month. The group provided alleged CCTV footage and computer system screenshots from these facilities as evidence. However, various media reports found that the claims of the attack were false, as they were found to be reusing photos and videos from another cyber group called Moses Staff.
On 25 November 2023, Cyber Av3ngers announced that it had hacked into a U.S. water authority in Aliquippa via a PLC device.
Matthew Mottes, the chairman of the water authority, confirmed that they were hacked by Cyber Av3ngers who took control of one of the stations.

Dragos believe that Cyber Av3ngers scanned the internet to identify accessible Unitronics devices, and then tried to log in using default credentials, which can be found in online operating manuals.
As a result, the U.S. Department of Homeland Security (DHS) Cybersecurity Infrastructure Security Agency (CISA) published an alert advising that facilities change the default “1111” password and set up multi-factor authentication, along with other recommendations.
The group continued its threats on the Cyber Av3ngers Telegram accompanied with messages such as “Good night Tel Aviv!” and “Don’t sleep too much at nights.” The Cyber Av3ngers have directly targeted Israel’s cyber defence chief, Gaby Portnoy, with warnings to remain vigilant.
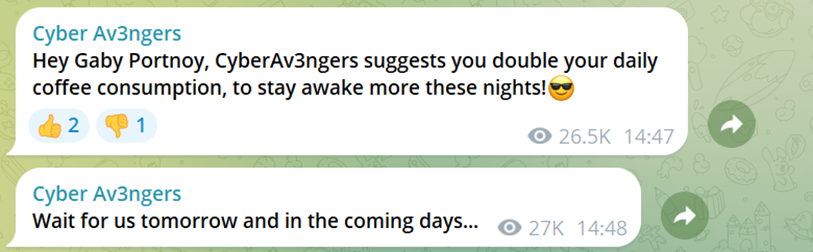
On X, the hackers categorise their account as “entertainment and recreation”, where they are also seen sharing their exploits.
In addition to the reward, the U.S. Treasury Department has imposed sanctions on the six Iranian officials, freezing their assets and prohibiting U.S. citizens from conducting business with them.
Brian E. Nelson, Under Secretary of the Treasury for Terrorism and Financial Intelligence, said: “The deliberate targeting of critical infrastructure by Iranian cyber actors is an unconscionable and dangerous act. The United States will not tolerate such actions and will use the full range of our tools and authorities to hold the perpetrators to account.”


































































































































































































































































































