North Korean spy chiefs are hacking into hospital computers to extort ransom payments which are then used to fund more cyber attacks, a new threat report warns. The communist state is using the attacks to fuel its nuclear ambitions, with the report from intelligence agencies in the US, UK, and South Korea, detailing a global espionage operation aimed at stealing critical technology.
The state-sponsored cyber group, identified as Andariel, is waging a campaign against organisations involved in defence, aerospace, nuclear, and engineering worldwide.
Andariel, also known as Onyx Sleet and APT45, operates within North Korea’s 3rd Bureau, the unit responsible for foreign intelligence.
The Department of Justice (DoJ) said: “The Andariel group is controlled by the DPRK’s military intelligence agency, the Reconnaissance General Bureau, which has primary responsibility for the DPRK’s malicious cyber activities and is also involved in the DPRK’s illicit arms trade.”
The group works to identify weaknesses in a system by using publicly available, internet scanning tools, and use the information they find for targeting.
Andariel hackers target corporations and government departments by uncovering weaknesses in their computer systems using publicly available internet scanning tools. Once software weak spots have been identified, hackers can exploit them to steal information, according to the report.
Andariel operators have also been accused of conducting phishing, attempting to trick people into giving them access by sending fake emails with harmful attachments.
Intelligence agencies caution that the group’s sophisticated tactics pose a persistent threat to the US, UK, South Korea, Japan, and India.
The report coincides with the indictment of an individual related to Andariel. The FBI have identified Rim Jong Hyok, who is wanted for his alleged role in ransomware attacks on U.S. hospitals and healthcare companies.
The ransomware payments, made in cryptocurrency, were laundered through Hong Kong-based intermediaries.
These funds were converted into Chinese yuan and withdrawn from ATMs in China.
The illicit proceeds were then used to lease virtual private servers, then used to launch attacks against defence, technology, and other organisations, aiming to steal sensitive information.
Hyok is accused of laundering money obtained through ransomware to further target 17 entities across the U.S. of including NASA and military bases.
The Department of State said: “In one computer intrusion operation that began in November 2022, the malicious cyber actors hacked a U.S.-based defence contractor from which they extracted more than 30 gigabytes of data, including unclassified technical information regarding material used in military aircraft and satellites, much of which was from 2010 or earlier.”

Hyok allegedly victimised five healthcare providers, which are prime targets for ransomware due to their heavy reliance on IT systems.
Laura Heuvinck, a spokesperson at the EU Agency for Cybersecurity, said: “The healthcare sector has been increasingly targeted as digitalisation has expanded the attack surface, giving rise to increased phishing and ransomware attacks.”
Alan Woodward, a computer security expert at the University of Surrey, added that hospitals are particularly at risk as they communicate between various providers making their systems more vulnerable.
The FBI’s Internet Crime Complaint Center identified healthcare as the top target for ransomware attacks in 2023.
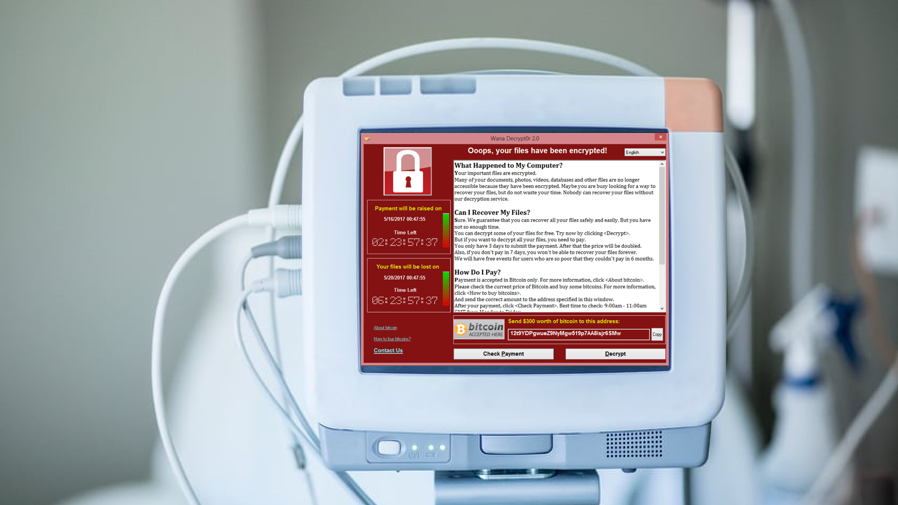
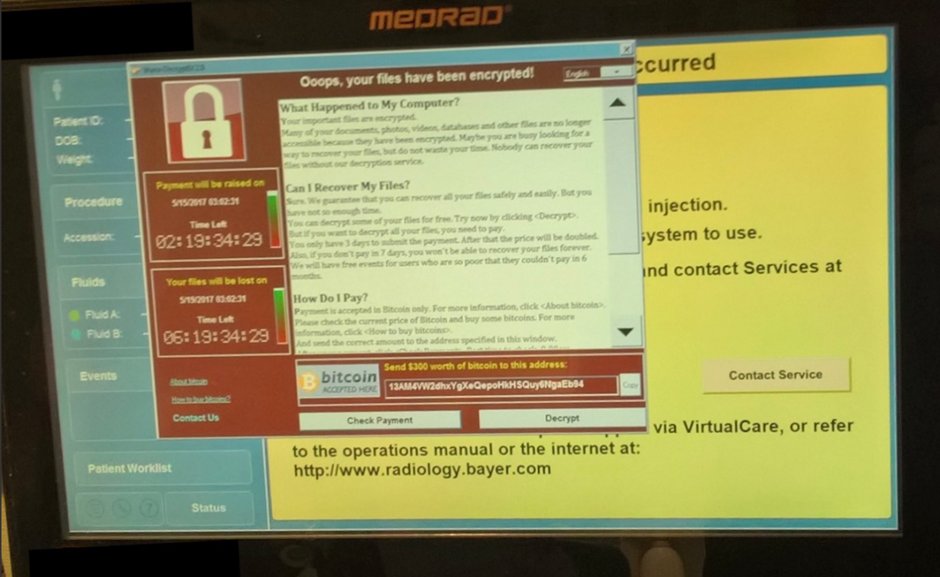
Rim and his co-conspirators developed a strain of ransomware called “Maui,” which according to the DoJ, prevented the healthcare provider from giving care to patients.
FBI Deputy Director, Paul Abbate, said: “These unacceptable and unlawful actions placed innocent lives at risk.”
The U.S. Department of State is offering a reward of $10 million for information leading to the location or identification of Hyok.
Cyber security firm Mandiant has uncovered a significant shift in North Korea’s cyber strategy, which reflects Pyongyang’s growing reliance on cyber operations to generate revenue.
The cyber firm said: “Financially motivated activity occurring alongside intelligence collection has become a defining characteristic of North Korean cyber operations, and we expect APT45 to continue both missions. As the country has become reliant on its cyber operations as an instrument of national power, the operations carried out by APT45 and other North Korean cyber operators may reflect the changing priorities of the country’s leadership.”
Their recent report, the result of a two-year investigation, states that the North Korean threat actor has been active in espionage campaigns since 2009.








































































































































































































































































