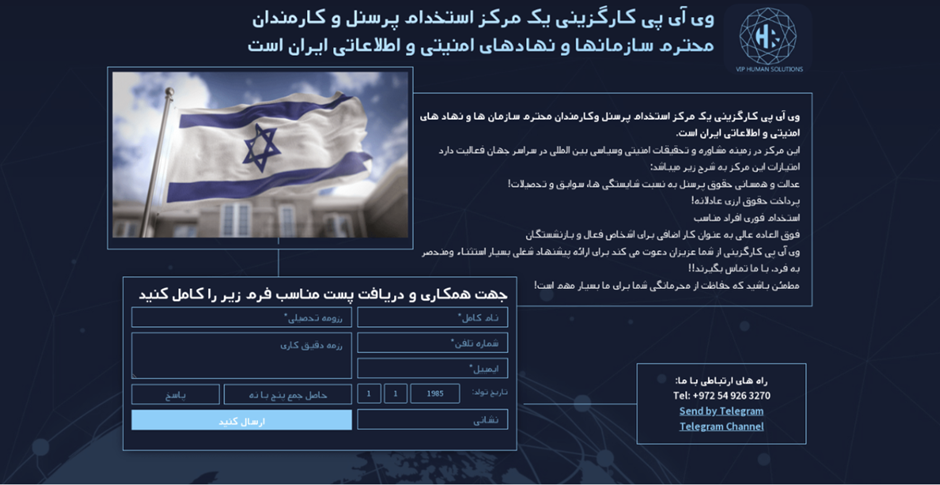
Iranian state-sponsored hackers have launched an espionage campaign targeting individuals perceived as threats to the regime. The cyber spies operate fake job websites, luring unsuspecting job seekers into giving up their personal information, which Iran then uses to spy on them.
The operation, uncovered by the U.S. cybersecurity firm Mandiant, dates back to 2017 and is believed to be part of a broader effort to silence those who oppose the Iranian regime, targeting Iranian dissidents, activists, and human rights advocates.
Ofir Rozmann, Mandiant APT researcher, told National Security News: “Iranian individuals targeted by this campaign may reveal themselves to the Iranian regime as Israeli/Western supporters, and interested in collaborating with Israeli entities.”
“Subsequently, Iran’s regime may investigate these individuals, conduct further operations against them (cyber and non-cyber) and persecute them,” Rozmann added.
Mandiant found over 35 websites disguised as legitimate recruitment sites. The digital traps offered attractive job opportunities for intelligence and security agencies and promised to protect the privacy of applicants.
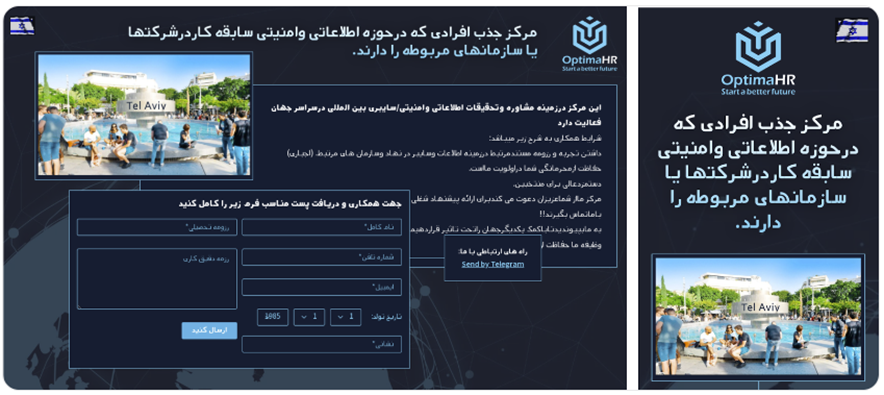
To enhance their credibility, the cyber criminals employed a variety of tactics. The websites featured “Israel-related lures” such as images of national symbols and flags, as well as hi-tech offices and major city landmarks.
Additionally, the contact details on the site listed Telegram links with handles containing “IL” (Israel) references, further reinforcing the campaign’s perceived affiliation with Israel, stated Mandiant.
Once the unsuspecting victims click “apply”, they are asked for personal details, including their name, birth date, email, home address, education, and professional experience. The sensitive information is then sent to the attackers.
While the campaign primarily targeted Farsi speakers, Mandiant identified similar operations aimed at Arabic-speaking individuals linked to Syria and Hezbollah. The websites were active between 2020 and 2023, and used a similar style and imagery. One of the websites called “VIP Recruitment” advertised as a recruitment centre for “respected military personnel”, displayed a picture of an Israeli flag.
To amplify their reach, Mandiant said that the cyber spies behind the campaign used fake social media accounts to publicise links to the malicious websites. Posts were made across platforms like X and Virasty, a social media platform that is commonly used in Iran.
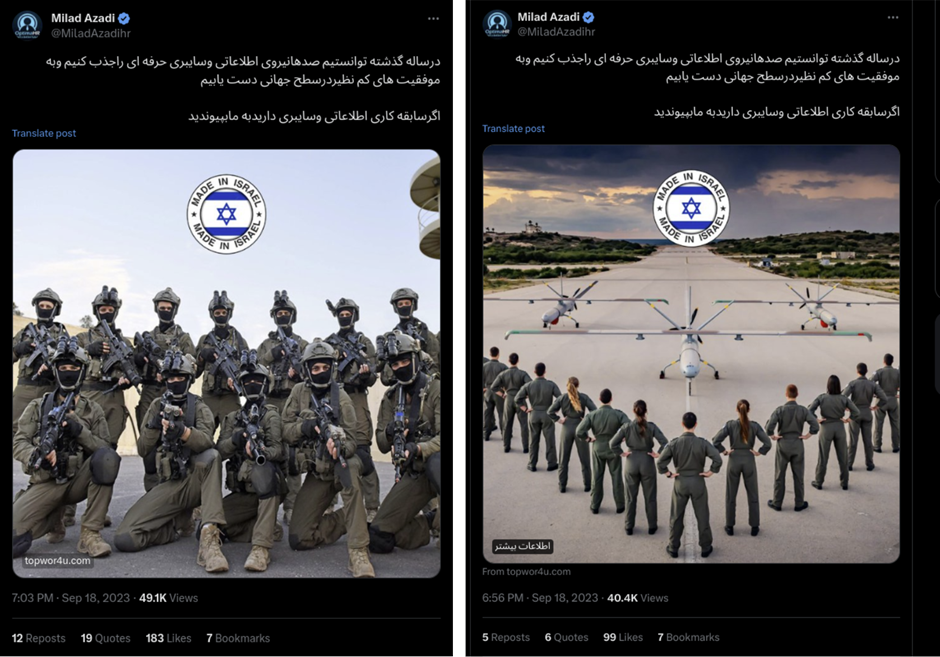
Rozzmann said: “Iran’s social engineering efforts are becoming increasingly sophisticated as time goes by. Individuals should be sure to carefully inspect job-related inquiries they receive over social media, as these continue to provide a fertile ground for various Iran-nexus cyber operations.”
Mandiant believes that the campaign is being operated on behalf of Iran’s regime, as the tactics and techniques used were similar to those of APT42, a group linked to Iran’s IRGC Intelligence Organisation. APT42 has a history of conducting surveillance operations against domestic threats and individuals of interest to the Iranian government.
Rozzman explained that users of Google Chrome and other browsers are now better protected against such activities, as the “SafeBrowsing” feature has successfully blocked the malicious infrastructure involved.


































































































































































































































































































