Ukrainian spy chiefs hunting for a “cyber bear” leading online attacks against electric and nuclear plants
UKRAINE’s spy agency is calling on its allies to help track down a spymaster it has linked to a Russian cyber unit coordinating online attacks on its bomb-ravaged cities.
It has identified Olga Viktorovna Dogonasheva as the Deputy Head of the state-sponsored Military Unit 71330, which is suspected of attempted hacks on electricity grids and nuclear plants across Ukraine.
The 43-year-old features on a list of 620 alleged Russian FSB officers, which was leaked en masse by the Intelligence Directorate of the Ukrainian Ministry of Defence back in March.
Russia has been launching missiles at Ukraine’s battered infrastructure pretty much continually since it launched the invasion in February, with bombing against civilian targets intensifying with each setback suffered by Putin’s military forces on the ground.
It has also conducted more than 1,500 cyber attacks against Ukraine in the first six months of the war, with Ukraine’s Oleh Derevianko telling National Security News (NSN) last month that he and colleagues were having to deal with hourly threats against companies and institutions.
Mr Derevianko, Chair of Information Security System Partners (ISSP), has been working with the US and other tech allies to repel the Russian threat.
Data analysts from NSN have established that Ms Dogonasheva is number 147 on the leaked list of FSB agents. In contrast to some of her spy contemporaries, however, Ms Dogonasheva, has been studious in leaving zero trace of herself on the world wide web.
Indeed, beyond the fact of the intelligence directorate recording that she was born in July 1979 in Vladivostok, a port city which borders China and North Korea, and listing her work address at the FSB HQ in Moscow, little is known about Ms Dogonasheva.
All traces of her education appear to have been removed from public databases, and there is no presence under her birth name on social media. To all intensive purposes she is a “ghost.”
According to security experts, this suggests that the FSB officer is living under a different legend – which could include a false passport and family history – making the task of hunting her down formidable.
Clues to her new identity may come from the nature of her work for Military Unit 71330, where hacks can be traced back to their point of origin.
The unit, also known as Centre 16, Energetic Bear and Crouching Yeti, operates from unmarked administrative buildings in hidden locations across Moscow, including secluded forest sites, where the only clue to their whereabouts is a cluster of satellites.
In March this year, the FBI charged four Russian employees from the unit with taking part in a hacking campaign that targeted thousands of computers at hundreds of worldwide companies between 2012 and 2018. The cyber attacks were mainly directed at oil installation, electricity plants, and other infrastructure facilities – and Military Unit 71330 has been repeating this systematic hacking in Ukraine since the start of the war.
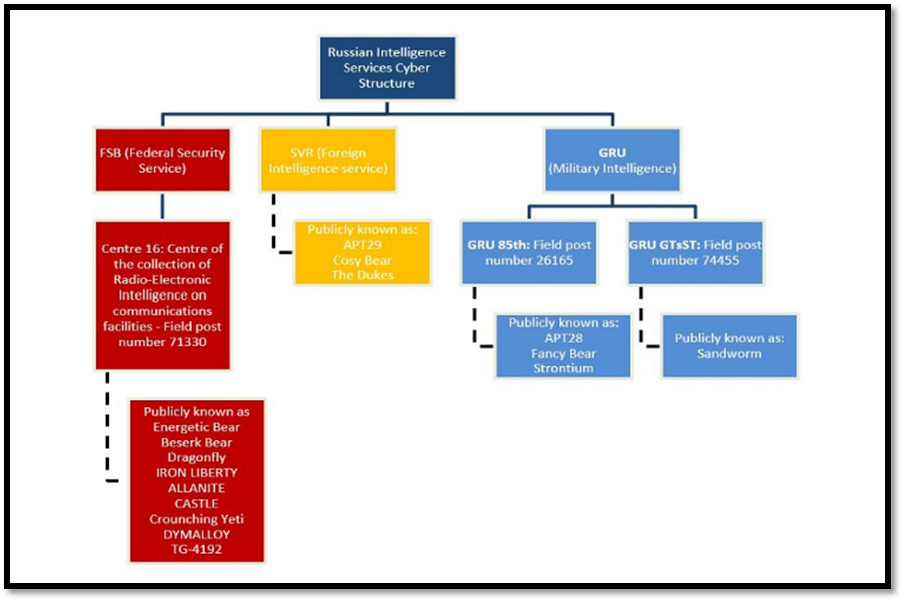
The unit is one of a string of intelligence corps overseen by various security and intelligence agencies, such as the Federal Security Service (FSB), Foreign Intelligence Service (SVR), and Military Intelligence Service (GRU), used to deploy destructive cyber attacks globally, each of which features names like Beserk Bear (FSB), Cosy Bear (SVR), and Fancy Bear (GRU).
Cyber attacks have become a major concern for global security, and Russia has become a significant threat to cyberspace, which has further escalated following its invasion of Ukraine.
When it comes to state-sponsored attacks, they are typically well resourced and highly sophisticated, allowing them to inflict immense harm on their targets.
John Lambert, Corporate Vice President of Microsoft Threat Intelligence Center said: “The sophistication and agility of attacks by nation state actors will continue to evolve. Organizations must stay informed of these actor changes and evolve their defenses in parallel”.
Russian cyber attacks against Ukraine have persisted ever since Russia’s illegal annexation of Crimea in 2014, intensifying just before the start of the current war on 24 February 2022.
Military Unit 71330 is the main structural unit of the FSB responsible for signals intelligence, which includes the interception, decryption and processing of electronic messages, as well as the technical penetration of foreign targets.
It has been widely identified as being behind cyber attacks against critical national infrastructure since at least 2010, targeting systems essential for energy, healthcare, finance, education and local/national governments.

Based on information released by the British government, Centre 16 compromised more than 1,000 energy companies in North America and Europe by malware attacks between 2013 and 2015.
A report by Symantec detailed the cyber unit’s campaign, which included attacks by spear phishing staff for their login credentials, or installing malware on their machines via booby-trapped webpages (watering hole attacks).
In 2017, the organisation conducted malicious cyber activity on UK companies associated with the energy sector. According to an investigation by Cylance, company systems were accessed using a bogus word document CV for someone called ‘Jacob Morrison’.
From 2020, the hackers focused their attention on the North American aviation sector, before also turning to US government networks, in one of the worst cyber espionage incidents in US history. This Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint alert on this activity.
US Deputy Attorney General Lisa Monaco said: “Russian state-sponsored hackers pose a serious and persistent threat to critical infrastructure both in the United States and around the world.”
Beyond the US, the cyber unit going by the name Energetic Bear stole data that affected Nato, the UK government, the European Parliament, and at least 200 more foreign organisations.
It was also involved in work against Kremlin critics, as it gained unauthorised access to the email address of an associate of Navalny and attempted to spear phish the press secretary of Mikhail Khodorkovskiy, a UK-based longstanding critic of the Kremlin.
According to data from Chainalysis, Russia-linked hackers are believed to have pocketed 74% of all the money made through ransomware attacks in 2021, amounting to more than $400m (US dollars) worth of crypto-currency payments. Cyber can be a source of income to the unprecedented economic costs imposed on Russia as a result of sanctions.
Microsoft has also reported in December that Russia is boosting its cyber activities in an attempt to “undermine US, EU, and Nato political support for Ukraine, and to shake the confidence and determination of Ukrainian citizens”. The report also added, “we believe these recent trends suggest that the world should be prepared for several lines of potential Russian attack in the digital domain over the course of this winter.”
Although its pseudonyms have varied from various ‘bear’ names to Dragonfly, Iron Liberty, Crouching Yeti, Dymalloy, the motive remains the same, to gather intelligence and sabotage.