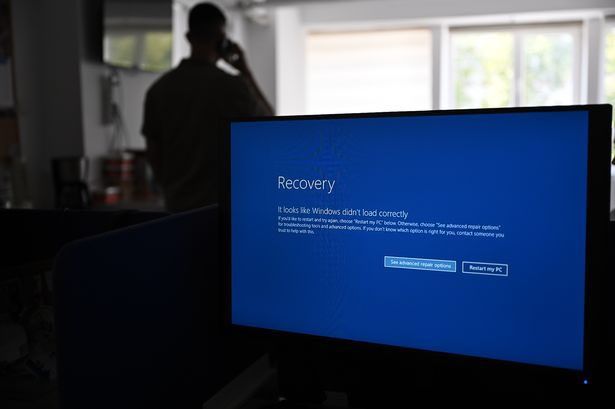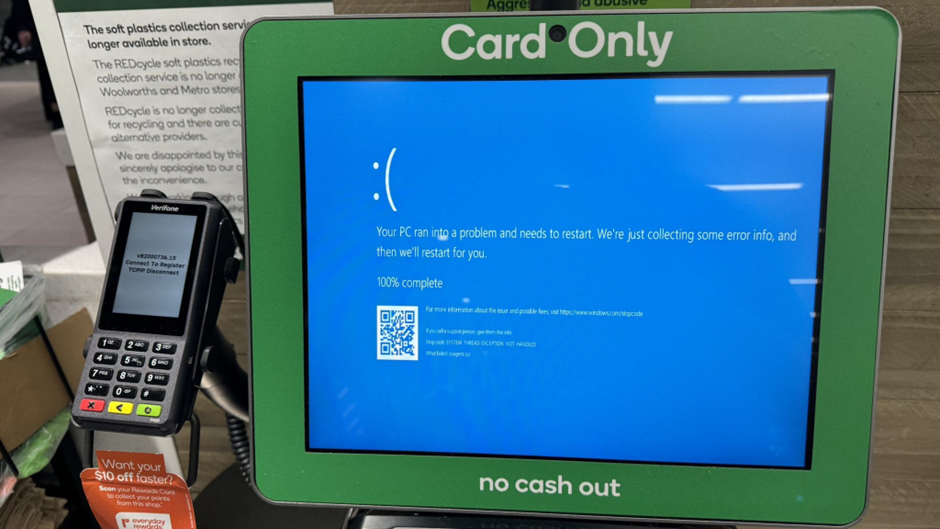
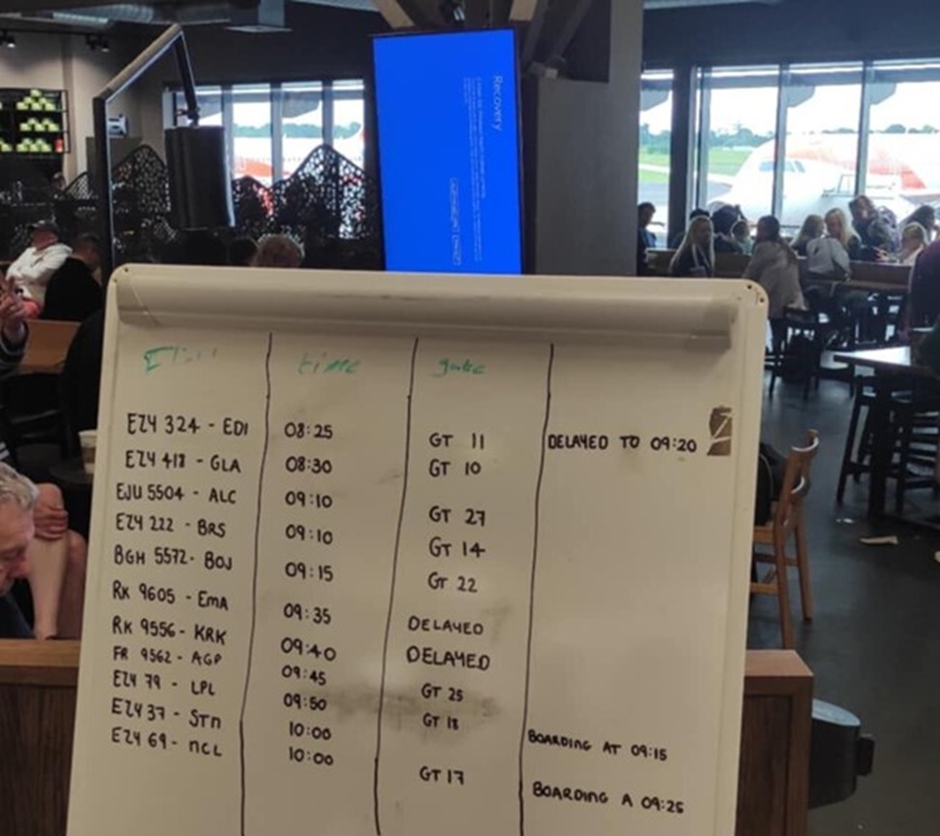
Anti-virus systems, like CrowdStrike which brought millions of Windows devices down, pose a potential security threat due to their trusted nature, according to Professor John Walker, a cyber consultant, who spoke to National Security News.
Continuous updates, he said, increase the chance of a faulty one slipping through and that anti-virus software is often seen as “secure’ by default leading to less scrutiny of updates.
Walker said: “From this point forward the world of cyber security needs to rethink what ‘trust’ really means in a very new light.”
“I would also add that this puts a whole new prospective on what we understand to be an ‘Insider Threat’,” Walker stated. This type of software, he said, interacts with many devices, amplifying the impact of a bad update.
What was a seemingly simple software update, is all it took for the world to experience digital chaos on 19th July. Airlines grounded flights, hospitals scrambled to maintain operations, and financial transactions stalled, all because of a faulty update from cybersecurity giant CrowdStrike.
Microsoft estimated that this incident impacted less than one percent of all Windows machines. David Weston, VP at Microsoft, said “While the percentage was small, the broad economic and societal impacts reflect the use of CrowdStrike by enterprises that run many critical services.”
But that one percent affected 8.5 million Windows devices.
What it illustrated according to Arno Robbertse, the Chief Executive Officer at ITC Secure “is that even well-established security providers can experience vulnerabilities.” He said it highlights “the need for rigorous testing, robust backup systems, and comprehensive incident response strategies.”
Ciaran Martin, ex-chief of Britain’s National Cyber Security Centre described it as “ very, very uncomfortable illustration of the fragility of the world’s core internet infrastructure.”
Brian Klass, associate professor in global politics at University College London stated: “For the billions of people who had never heard of CrowdStrike, it was a crash course in a disturbing fact: much of our world runs on software from companies that, when they make a mistake, can bring down the fundamental systems that run our world, from travel to banking and healthcare.
“A tiny local mistake can now be amplified into a dystopian global cascade — and we are lucky that this debacle wasn’t much worse,” Klass added.
Professor Feng Li, Associate Dean of Research and Innovation at University of London, said “It is surprising that lessons from the past haven’t been learned and that this could happen today, at such a massive scale around the world. It’s not just CrowdStrike’s fault. Although it is sensible to give an antivirus company privileges to update their systems, a robust [operating systems] shouldn’t let things like this happen.”
So, what should be done next to prevent a recurrence or even worse, the possibility that fragility could be weaponised into a full-blown cyber-attack?
Arno Robbertse highlights the critical importance of resilience in our increasingly digital world and told NSN that the CrowdStrike incident underscores “the need for rigorous testing, robust backup systems, and comprehensive incident response strategies.”
“With the upcoming EU Digital Operational Resilience Act (DORA) set to impose stringent requirements on financial entities, it’s imperative for businesses to not only comply with these regulations but to also embrace a culture of continuous improvement and proactive risk management.”
DORA, Robbertse said, aims to ensure that financial institutions can withstand and quickly recover from all types of IT disruptions, making resilience not just a regulatory requirement, but a competitive advantage.
He also highlighted the issue of a global security personnel shortage.
“Being able to be resilient requires you to have the right people, process and technology in place. The former can be a real challenge when you consider the global security personnel shortage. Working with the right security partners as an extension to your existing teams has never been more important,” Robbertse noted.
The CrowdStrike error is not the first time an update has brought down computer systems. In 2010, McAfee released an antivirus software update for its corporate customers, which mistakenly deleted a crucial Windows file, sending systems crashing.
Following the incident, users on X pointed out that George Kurtz, co-founder and CEO of the firm, was the CTO of McAfee when the company faced the technical failure in 2010.