RANSOMWARE attacks are expanding at such an exponential rate that they will cost the global economy ten trillion dollars ($10 trillion) by 2025, according to an influential new study.
The figure came from researchers at the European Union Agency for Cybersecurity (ENISA), which has been monitoring cyber-crime across the world since 2004.
The Athens-headquartered organisation arrived at its projection after analysing 623 ransomware incidents which took place between May 2021 and June 2022.
And ENISA’s “Threat landscape for Ransomware Attacks” makes chilling reading.
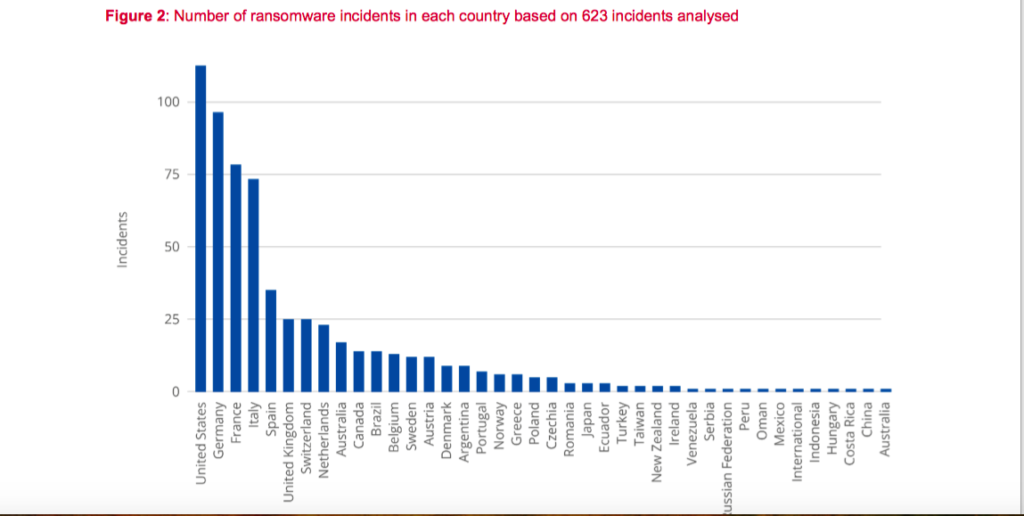
It reveals how ransomware has now become a franchise commodity where a cyber-criminal with even basic computer skills can quickly target companies and individuals pretty much anywhere around the world – with the USA (112 recorded incidents 2021-2022), Germany (96), and France (78) the most targeted countries.
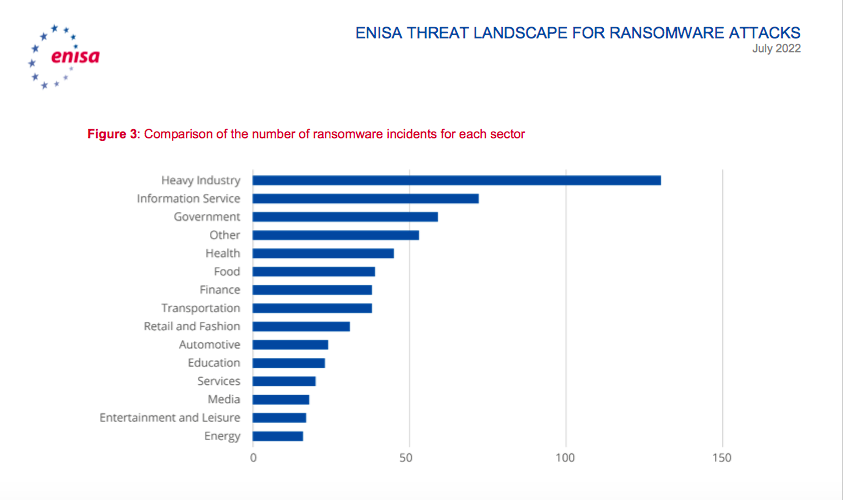
The sectors most heavily targeted were so-called “heavy industry” – which would include oil and gas refineries global shipping, and large-scale manufacturing plants. Governments were also targeted, as were Information Services, and health sectors.
In more than 95.3% of incidents, victims of cyber-crimes did not know how the ransomware threat actors had gained access to their systems.
The report stated: “Interestingly, from our previous analysis of leaked data, we found that 37.88% of the targets had their data fully leaked on the Internet. This suggests, but does not imply, that around 62.12% of the incidents might have actually paid the ransom, and that is why their data was not leaked.”
Adding: “Of course, there are many mitigating situations, such as targets that paid and their data was leaked anyway, or targets that did not pay and their data was not leaked. However, the estimation of 62.12% is very close to the result of a survey from the Claroty security company that found that 62.14% of the respondents confirmed that their company paid the ransom. Although these numbers should not be taken as a guide because they are merely indicators, they certainly bring the problem into focus.”
ENISA said the findings are “grim,” adding that businesses needed to be “ready for the possibility of their assets being targeted by ransomware, but also to have their most private information stolen and possibly leaked or sold on the internet to the highest bidder.”
And while financial inducement was the most common motivation for online blackmail, cyber criminals were also asking for changes in corporate policy, new software features, and asking targets to infect their social circle.”
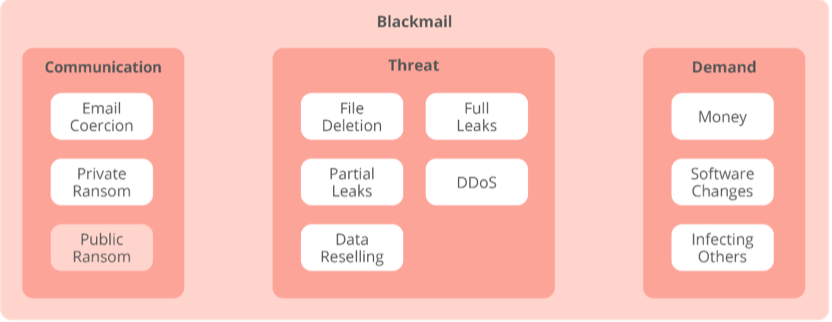
An evolving feature of ransomware identified by the report’s authors was “data brokerage,” where stolen data was sold on.
“In this model, threat actors take further advantage of the stolen data by selling it to the highest bidders. This also includes reselling the access obtained to the target to other threat actors for additional exploitation,” the report added.
The report recommended potential targets take the following steps:
- Keep an updated backup of your business files & personal data. Keep this backup isolated from the network;
- Apply the 3-2-1 rule of backup: 3 copies, 2 different storage media, 1 copy offsite;
- Run security software designed to detect most ransomware in your endpoint devices; and
- Restrict administrative privileges.
If you fall victim of a ransomware attack:
- Contact the national cybersecurity authorities or law enforcement for guidance;
- Do not pay the ransom and do not negotiate with the threat actors;
- Quarantine the affected system; and
- Visit the No More Ransom Project, a Europol initiative.
















































































































































































